Important announcement
After many thoughts, we have to put a term to orWall dev. The code won't be updated anymore (and hasn't be for ages), and it still has some security flaws as you might see in the opened issues.orWall
Put your apps behind Orbot and block all unwanted traffic in one go.
Be careful!
This application takes care of your connection, NOT what's your sending or receiving! This means you must use applications providing enough privacy in order to avoid sending out your complet device information.
We were told some people seem to use orWall on their android device with stock browser. Without any settings. Meaning they are sending away their information like browser type, device type and, even, MAC or some hash strings.
Of course this isn't the right way to use Tor or any other Onion Router system.
Of course this is the best way for you to be tracked down.
Please be sure of what you're doing. If you want to visit hidden services, please use Orfox or any privacy-aware browser! orWall doesn't take care of what your apps send to the Net. At all. And won't do it. Never. This is not orWall goal. And will never be.
How does it work?
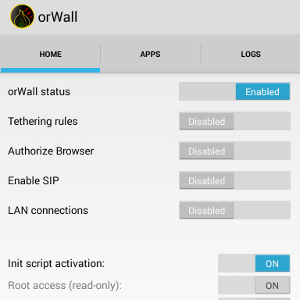
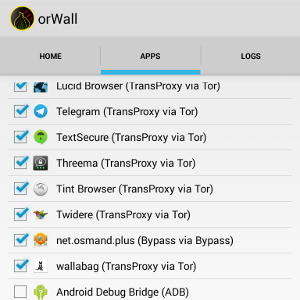
orWall will force selected applications through Orbot while preventing unchecked applications to have network access.
In order to do so, it will call the iptables binary. This binary, present on your Android device, requires superuser access (aka root). It's the application that manages the firewall on Linux and, by extension, on Android.
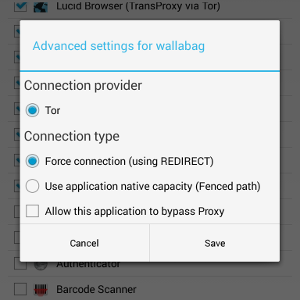
In short, orWall will add special iptables rules in order to redirect traffic for applications through Tor; it will also add required rules in order to block traffic for other apps.
The redirection is based on the application user id. Each android application runs as a dedicated user, and iptables has support for traffic filtering based on the process owner, meaning it's really easy and pretty safe to do this kind of thing on an Android device.
Limitations
This application takes care of IP connections only, not GSM. It won't protect you if an attacker sends commands to your baseband through SMS, for example.
Also, on some Android versions (at least 4.1.1), the init-script will not work, meaning you may have outgoing connections before orWall starts.
The application works in two stages: first, an init-script will block all incoming and outgoing traffic. This should prevent leaks, knowing Android sends stuff before you can even access the device.
Second stage comes once the device is fully booted: orWall itself takes the lead on the firewall, and add required rules in order to allow Orbot traffic, and redirect selected application to Orbot TransPort.
Basically, orWall is a simple UI for scripts provided by in his blog post on torproject.
A felelős játék elvének betartása minden online kaszinó működésének alapvető követelménye kell, hogy legyen.
What orWall is
- A firewall configurator: it allows you to set up your device in order to force apps through Orbot.
- A way to prevent unwanted network access: only the apps you select access the Net through Orbot.
- An app you should use with caution: if you don't understand what it's doing, you may have some bad surprises.
What orWall isn't
- A replacement for Orbot: you still need Orbot on your device.
- A replacement for AFWall/DroidWall – but it may lead to weird problems if you're using both.
- The Answer to the Ultimate Question of Life, the Universe and Everything: everybody knows it's 42.
Prerequistes
- Root access
- Orbot
How to use orWall
- Ensure you have Root access on your device.
- Ensure you don't have AFWall or other firewall manager installed, or at least deactivate them
- Ensure you have Orbot installed.
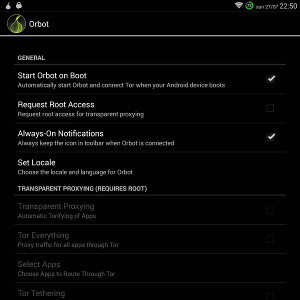
- Ensure Orbot has no Transparent Proxy enabled, like on the screenshot.
- Start orWall , select the apps you want to redirect to Orbot.
- Reboot.
- Enjoy more privacy!
We strongly recommend you use Guardian Project f-droid in order to get the latest Orbot version available.
Troubleshooting
- No network anymore: Did you start Orbot? Did you select applications? Do you have network (i.e. wireless, 3G and so on)?
- No network anymore (bis): Ensure you don't have Transparent Proxy enabled in Orbot.
- No network anymore (tris): Is Orbot connected to the Tor Network?
- My apps aren't going through Tor: Are you using some other firewall application, like AFWall or DroidWall? If so, please remove it, reboot, and test again.
- Application crashes with no message: Please fire up ADB logcat and fill in a new issue. :)
- Some menu entries are disabled: Did you activate those options in the settings? Did you select Browser app and/or SIP app in the settings?
How to uninstall orWall
- Remove the init-script (from the settings)
- Uninstall the app as usual.
- Reboot.
We cannot catch the uninstall event in order to make things, meaning you have to remove the init-script by hand.
In case the init-script is still present, you can remove it from the shell (ADB or any root-supporting Terminal application):
su mount -o remount,rw /system rm -f /system/etc/init.d/91firewall mount -o remount,ro /system reboot
How to request support?
Please open an issue with the following information:- Device model;
- Android version;
- orWall version;
- Steps to reproduce the problem;
- LogCat output;
- screenshots (if possible);
- Output of
iptables -vnLandiptables -vnL -t nat;
I want to take part!
Great news, thanks! Just create a fork and submit pull-requests. We're opened for new features, bug corrections and so on, feel free to help.
We're seeking people for translations, bug swatting, read proofing.
We're also wanting to add the following features to orWall:
- Action: when we deselect an app in orWall, it should be restarted in order to ensure network is cut.
- Action: panic button: allow user to cut all connections in one shot (though it's possible to do so by cutting Orbot).
- When we remove an application, it should be removed from orWall authorization list in order to prevent UID overlaps.
Screenshots
They speak about orWall
- The Daily Dot — 08.10.2014 "The 3 apps you need to use your Android phone anonymously"
- Tor Weekly News — 08.10.2014
- is willing to promote orWall
- Numerama — 30.07.2014
Latest Posts:
What about the previous name, Torrific?
There's a trademark on "Tor", and it seems Tor Project wants to enforce it. Kindly, that said (and I emphasize this fact). So, in order to both respect the trademark and avoid useless discussions, I prefered to change the name to something else. All is fine now :).
Long live orWall, your new Onion Router Firewall!